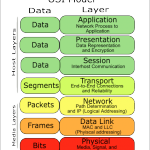
Repeater: A repeater’s job is to repeat an electrical signal. The form that our data has taken to be sent across a cable is one’s and zeros. The repeater takes an incoming signal and then generates a new clean copy of that exact signal. This prevents maximum cable lengths from stopping transmissions and helps ward off attenuation; the gradual weakening of a signal.
Hubs – only one PC at a time can send data; if multiple PC’s are connected to a single hub, it’s One Big Collision Domain. To prevent collisions, a host will use CSMA/CD (Carrier sense multiple access with collision detection).
CSMA/CD:
- a carrier sensing scheme is used.
- a transmitting data station that detects another signal while transmitting a frame, stops transmitting that frame, transmits a jam signal, and then waits for a random time interval before trying to send that frame again.
Bridge – used to create smaller collision domains. Place a bridge between multiple hubs. More collision domains is more beneficial. Segmenting the collision domains does not reduce the amount of broadcasts (for example, multiple hubs separated by multiple bridges is still one big broadcast domain). Every single host will receive a broadcast.
Broadcasts are not a bad thing, broadcasts can be beneficial by providing routing updates. But we do want to lower the number of broadcasts.
Switches: each host is in it’s own collision domain. Collisions cannot occur. Each host has more bandwidth available; not sharing bandwidth. Theoretically each host can run at 200mb (100mb sending, 100mb receiving with full duplex). Switches by default do not break up broadcast domains. Microsegmentation is a term sometimes used with Cisco documentation to describe the one host/one collision effect.
A switch will do one of three things with an incoming frame:
- Forward it
- Flood it
- Filter it
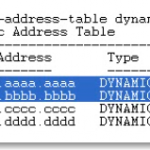
The switch looks at it’s Mac address table to check if there is an entry for the destination MAC address, but first the switch will look to see if there’s an entry for the source MAC address in the frame. The switch uses the source MAC address to build the table. You can statically configure MAC address tables but not recommended.
#show mac-address-table — The command we use to look at the mac address table on a switch.
An unknown UNICAST frame is always flooded. – If an unknown unicast frame has to hit 79 other ports in an 80 port switch, it can cause a bit of overhead on the switch/cpu.
#show mac-address-table dynamic
If the switch does not have an entry for the destination mac address, and a host replies to the flood with the correct response, the switch will create an entry for the new host.
Take into consideration the following diagram:
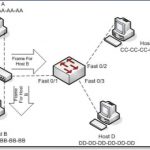
In this instance, hosts A and B are in the same collision domain, separated by a hub. When Host A sends out a frame destined for Host B, and the frame arrives at the switch, the switch looks at it’s dynamic MAC address table and sees that the frame is destined for the same port as it’s origin. In this case the switch will FILTER the frame (drop the frame):
Switches never send a frame back out the same port from which the frame arrived.
Flooding: When the switch has no entry for the frame’s destination MAC address. The frame is sent out every single port on the switch except the one it came in on. Unknown unicast frames are always flooded.
Forwarding: when the switch does have an entry for the frame’s destination MAC address. Forwarding a frame means the frame is being sent out only one port on the switch.
Filtering: when the switch has an entry for both the source and the destination MAC address; the MAC table indicates that both addresses are found on the same port. (See image above)
Broadcast frames: a frame that is sent out every port on the switch except the one that received it. Broadcast frames are intended for all hosts, and the MAC broadcast address is ff-ff-ff-ff-ff-ff.
We can statically configure a port with a MAC address but not best practice. Dynamically learned MAC addresses will age out with a default of 300 seconds (5 minutes).
Command to see help for the tables is
#mac-address-table ?
then
#mac-address-table aging-time ?
0-0 Enter 0 to disable aging (not a good thing to do)
10-1000000 Aging time in seconds
The benefit of Dynamically configured MAC addresses is that if the host is not seen in 5 minutes or the interface goes down; physical damage to the port, when the host is connected to a different port, the switch will dynamically update the table with the source. The current entry will be aged out. Let the switch do it’s work, and use dynamically assigned addresses.
When the switch forwards, floods, or filters the frame, there is another decision to be made – how will the forwarding be processed?
Three different processing options:
- Store-And-Forward
- Cut-Through
- Fragment-Free
Store and Forward is the default method on newer switches. The entire frame is stored and then forwarded.
Store and Forward – uses FCS – allows the recipient of the frame to determine if the data was corrupted during transmission (error detection). In the incoming frame the switch will read the destination MAC address before it looks at the FCS. The switch can check the FCS before forwarding the incoming frame. Gives us more error detection than the other two methods above.
Cut-Through – switch reads the MAC addresses on the incoming frame, and immediately begins forwarding the frame before rest of the frame is even read. Cut through is a lot faster. Cannot check for damaged frames.
Fragment-Free (middle ground for speed vs. error detection) works on the presumption that the corruption will be found in the first 64 bytes of the frame for damage. If no damage, then the forwarding process will begin.
Use virtual LANs to segment a network into smaller broadcast domains. In a production network, you can have a lot of hosts and each host can send out broadcasts with a cumulative effects. Hosts tend to respond to Broadcasts with a Broadcast of their own.
Broadcast Storm: can max out a switch’s resources (memory and cpu) making the switch useless. But before this, broadcasts may take up most of the bandwidth.
Create multiple broadcast domains to limit the scope of a broadcasts.
Basic command to view vlans is
#show vlan
but for practical use, the command below is better:
#show vlan brief
By default, you will have a single vlan on modern cisco switches.
To put for example two hosts in a separate single vlan (broadcast domain),
#conf t
#interface fast 0/2
#description Connected to Host 2
#switchport access vlan 24
#switchport mode access — to makes access to only one vlan – no trunking
then
#int fast 0/4
#description Connected to Host 4
#switchport mode access
#switchport access vlan 24
#^Z
#copy run start
#show vlan brief
Once host2 and host4 are on the same vlan they won’t be able to ping other hosts on other vlans.
No traffic – pings or data packets can be sent from one VLAN to another without intervention of a Layer 3 device; most likely a router.