If you’ve got a new MacPro and want to utilize both of the two built-in Gigabit Ethernet ports (and possibly some Thunderbolt-to-ethernet adapters) in a bonded LACP Link Aggregation virtual adapter in conjunction with a Cisco 3750 switch, follow the instructions below.
The first part is configuring your switch to allow your Mac to create a bonded link. In my case, without first configuring the switch, I was able to create my Mac’s bonded ethernet adapters, but couldn’t pick up a DHCP address. I further went into the virtual adapter’s bond status and saw red dots and the messages “No Partner” and/or “Bad Link”. The problem was that I hadn’t setup my switch with the appropriate LACP protocol on it’s interfaces.
Here are the instructions for creating a bonded Ethernet LACP link aggregation from Apple: http://support.apple.com/kb/PH8356
Note that in the above article there are some requirements: you need at least one IEEE 802.3ad-compliant switch or another Mac OS X Server computer with the same number of ports.
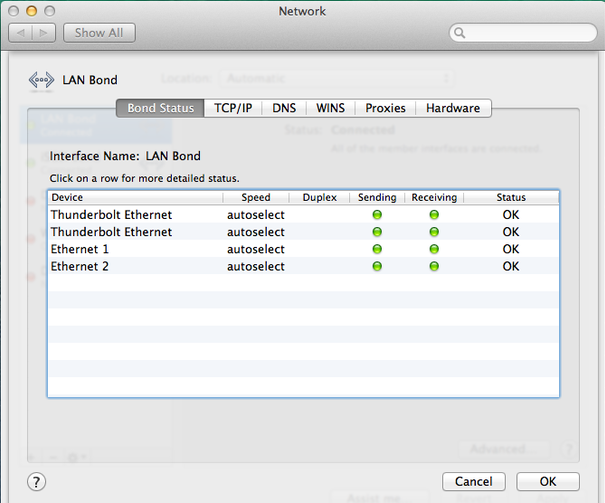
So I configured a Cisco 3750 switch with a new channel group, and added 4 ports into the channel group so that we can bond 4 NICs for the MacPro’s LAN connection at 4GBps
Here is the channel group configuration
!
interface Port-channel2
description LAN Etherchannel Team for MacPro
switchport access vlan 27
switchport trunk encapsulation dot1q
switchport mode access
!
And here are the gigabit interfaces configuration
!
interface GigabitEthernet1/0/13
description MacPro Eth1 to LAN
switchport access vlan 27
switchport trunk encapsulation dot1q
switchport mode access
channel-protocol lacp
channel-group 2 mode active
!
interface GigabitEthernet1/0/14
description MacPro Eth2 to LAN
switchport access vlan 27
switchport trunk encapsulation dot1q
switchport mode access
channel-protocol lacp
channel-group 2 mode active
!
interface GigabitEthernet1/0/15
description MacPro ThunderBolt BottomLeft to LAN
switchport access vlan 27
switchport trunk encapsulation dot1q
switchport mode access
channel-protocol lacp
channel-group 2 mode active
!
interface GigabitEthernet1/0/16
description MacPro ThunderBolt BottomRight to LAN
switchport access vlan 27
switchport trunk encapsulation dot1q
switchport mode access
channel-protocol lacp
channel-group 2 mode active
!
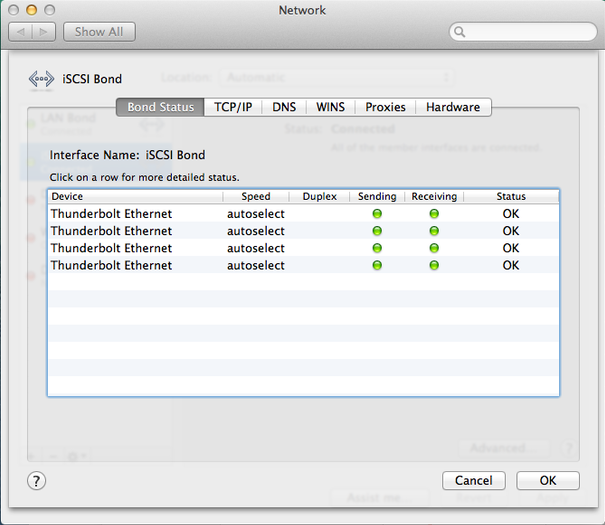
I further went on to create another 4xThunderbolt Ethernet Adapter for an iSCSI connection to a NAS by creating a new channel group 3 and added the remaining 4 thunderbolt interfaces into group 3:
!
interface Port-channel3
description iSCSI Etherchannel Team for Mac Pro
switchport access vlan 27
switchport trunk encapsulation dot1q
switchport mode access
!
…
…
…
!
interface GigabitEthernet1/0/17
description MacPro TB iSCSI
switchport access vlan 27
switchport trunk encapsulation dot1q
switchport mode access
channel-protocol lacp
channel-group 3 mode active
!
interface GigabitEthernet1/0/18
description MacPro TB iSCSI
switchport access vlan 27
switchport trunk encapsulation dot1q
switchport mode access
channel-protocol lacp
channel-group 3 mode active
!
interface GigabitEthernet1/0/19
description MacPro TB iSCSI
switchport access vlan 27
switchport trunk encapsulation dot1q
switchport mode access
channel-protocol lacp
channel-group 3 mode active
!
interface GigabitEthernet1/0/20
description MacPro TB iSCSI
switchport access vlan 27
switchport trunk encapsulation dot1q
switchport mode access
channel-protocol lacp
channel-group 3 mode active
!
Lastly I created a new iSCSI Bond on the MacPro successfully and provided the Bond adapter with a Manual Address 192.168.27.30.
Doing this left me with:
4GB bonded connection to LAN
4GB bonded connection to iSCSI NAS complete
Here’s what the 2nd bond looks like in ifconfig:
bond1: flags=8843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST> mtu 1500
options=b<RXCSUM,TXCSUM,VLAN_HWTAGGING>
ether 68:5b:35:b9:4a:3a
inet6 fe80::6a5b:35ff:feb9:4a3a%bond1 prefixlen 64 scopeid 0x16
inet 192.168.27.30 netmask 0xffffff00 broadcast 192.168.27.255
nd6 options=1<PERFORMNUD>
media: autoselect (1000baseT <full-duplex>)
status: active
bond interfaces: en15 en13 en16 en14
Here’s what the beast looks like from the outside:

Test I/O and copy speed results:
50GB of data copied with my new favorite file copy utility “bvckup2” from Server to NAS in 6 minutes, 45 seconds (!) utilizing 25% iSCSI Team 3Gbps around 104 MB/sec.
50GB of data copied with Windows copy/paste from Server to NAS utilizing 26% iSCSI Team 3Gbps in 7 minutes, 2 seconds.
… As opposed to 50GB over a USB 2.0 connection = 24hrs
… As opposed to 50GB over 10/100 LAN at 10MB/sec = 83 min
… As opposed to 30MB/sec on average gigabit LAN = 27 min
… As opposed to well-optimized Gigabit network around 60 MB/sec = 15 min
…As opposed to transfer speed record set on Feb 25, 2014 Sending data at a rate of 64 gigabits per second (Gb/s)(!?)