Ensuring your secondary WAN interface activates in the event either your primary router or primary ISP stops responding.
In the previous post, we discussed how businesses are increasingly relying on their internet for cloud-based services such as email, shared documents and applications. Using multiple SonicWALL appliances and multiple WAN/ISP interfaces, you can help protect your users from an internet outage by configuring your routers to fail-over. A SonicWALL can perform either interface or physical probing.
If Probe Monitoring is not activated, the SonicWALL security appliance performs physical monitoring only on the Primary and Secondary WAN interfaces, meaning it only marks a WAN interface as Failed if the interface is disconnected or stops receiving an Ethernet-layer signal (Layer 2).
This is not an assured means of link monitoring, because it does not address most failure scenarios (for example, routing issues with your ISP or an upstream router that is no longer passing traffic). If the WAN interface is connected to a hub or switch, and the router providing the connection to the ISP (also connected to this hub or switch) were to fail, the SonicWALL will continue to believe the WAN link is usable, because the connection to the hub or switch is good. For this reason, if you setup failover with multiple routers, then you will also want to enable a TCP-based probe at the application Layer 4 so that you can ensure your packets/probes are monitored for successful connections, and your WAN fail-over will in turn work as expected.
Under the WAN Interfaces Monitoring heading, you can customize how the SonicWALL security appliance monitors the WAN interface:
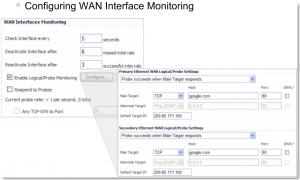
This example shows how a probe is configured correctly where you’re monitoring for successful (syn-ack’s) from google.com.
Options and Notes:
Check Interface every: Enter a number between 5 and 300. The default value is 5 seconds.
Deactivate Interface after _ missed intervals: Enter a number between 1 and 10. The default value is 3, which means the interface is considered inactive after 3 consecutive unsuccessful attempts.
Reactivate Interface after _ successful intervals: Enter a number between 1 and 100. The default value is 3, which means the interface is considered active after 3 consecutive successful attempts.
Respond to Probes: Use this field to allow the SonicWALL security appliance respond to SonicWALL TCP probes received on any of its WAN ports.
Any TCP-SYN to Port: Use this field to instruct the SonicWALL security appliance to respond to TCP probes to the specified port number without validating them first. The Any TCP-SYN to Port box should only be checked when receiving TCP probes from SonicWALL security appliances running SonicOS Standard or older, legacy SonicWALL security appliances.
Note: If there is a NAT device between the two devices sending and receiving TCP probes, the Any TCP-SYN to Port box must be checked and the same port number must be configured here and in the Configure WAN Probe Monitoring window.
Configure Probe Monitoring
Enable Logical/Probe Monitoring: Selecting this field instructs the SonicWALL security appliance to perform logical checks of upstream targets to ensure that the line is indeed usable, eliminating this potential problem, as well as to continue to do physical monitoring. Under the default probe monitoring configuration, the SonicWALL performs an ICMP ping probe of both WAN ports’ default gateways. Unfortunately, this is also not an assured means of link monitoring, because service interruption may be occurring farther upstream. If your ISP is experiencing problems in its routing infrastructure, a successful ICMP ping of their router causes the SonicWALL security appliance to believe the line is usable, when in fact, it may not be able to pass traffic to and from the public Internet at all.
To perform reliable link monitoring, you can choose TCP or ICMP (Ping) as the monitoring method, and can specify up to two targets for each WAN port. If you specify two targets, Main Target and Alternate Target, for each WAN interface, you can logically link the two probe targets so that if either one fails, the line will go down, or that both must fail for the line to be considered down. TCP is preferred because many devices on the public Internet now actively drop or block ICMP (Ping) requests.
SNWL?: Select this box if the target device is a SonicWALL security appliance. Do not check the SNWL? box for third-party devices, because the TCP probes may not work consistently.
Default Target IP: Optionally, you can enter a default target IP address in the Default Target IP field. In case of a DNS failure, when a host name is specified, the default target IP address is used.
There is much discussion below on the best strategies for setting up your probes. As always, test (and test again) your configurations in the lab prior to placing your firewall into production.

What are good addresses or sites to use for WAN probes?
I use google, but thinking what other site would be good to poll?