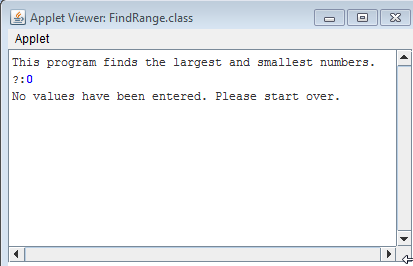
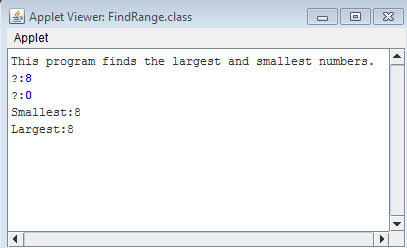
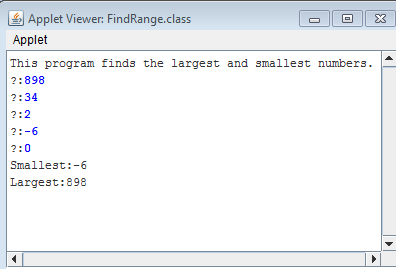
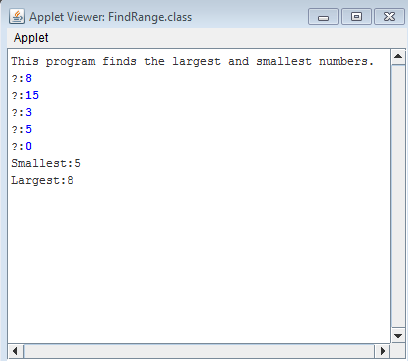
The problem is as follows:
Create a figure that is simply three GOval objects, two red and one white, drawn in the correct
order. The outer circle should have a radius of one inch (72 pixels), the white circle
has a radius of 0.65 inches, and the inner red circle has a radius of 0.3 inches. The
figure should be centered in the window of a GraphicsProgram subclass.
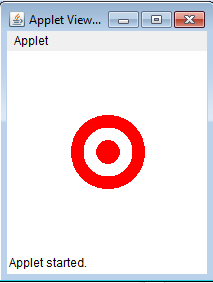
Here is my first part of the solution to the problem. The output is correct, however, the guide states I should use constants. I will re-write the program later in Part 2 once I have learned how to use constants. But for now here is the solution to the problem and the output below.
/*
* File: Target.java
* Name: Jason Coltrin
* Section Leader: n/a
* -----------------
* This file is the starter file for the Target problem.
* This figure is simply three GOval objects, two red and one white, drawn in the correct
* order. The outer circle should have a radius of one inch (72 pixels), the white circle
* has a radius of 0.65 inches, and the inner red circle has a radius of 0.3 inches. The
* figure should be centered in the window of a GraphicsProgram subclass.
*/
import acm.graphics.*;
import acm.program.*;
import java.awt.*;
public class Target extends GraphicsProgram {
public void run() {
drawLargeRedOval();
drawWhiteOval();
drawSmallRedOval();
}
// precondition: a canvas of 200pixels across and 200pixels top to bottom,
// the center is 100x100 pixels.
// postcondition is a red filled circle with 1 inch radius with 72pixels has
// a center of 36
// 100 - 36 = 64,64 is where the left and bottom of the rectangle in which
// the oval is located should be placed
public void drawLargeRedOval() {
GOval myOval = new GOval(64, 64, 72, 72);
myOval.setFilled(true);
myOval.setColor(Color.RED);
myOval.setFillColor(Color.RED);
add(myOval);
}
// precondition: a 200x200pxl canvas with a 72pxl red circle centered at
// 100x100
// postcondition: another white circle added on top of the red circle. .65
// of 72 = 46.8 - half of 46.8 = 23.4
// 100 - 23.4 = 76.6, is where the left and bottom of the GOval rectangle is
// set.
public void drawWhiteOval() {
GOval myOval = new GOval(76.6, 76.6, 46.8, 46.8);
myOval.setFilled(true);
myOval.setColor(Color.WHITE);
myOval.setFillColor(Color.WHITE);
add(myOval);
}
// precondition: a 200x200pxl canvas with a 46.8 white circle on top of a
// red 72pxl circle with a center of 100x100
// post condition: another red circle added on top of the white circle. .3
// of 72 = 21.6 - half of 21.6 = 10.8
// 100 - 10.8 = 89.2, is where the left and bottom of the small re oval is
// set.
public void drawSmallRedOval() {
GOval myOval = new GOval(89.2, 89.2, 21.6, 21.6);
myOval.setFilled(true);
myOval.setColor(Color.RED);
myOval.setFillColor(Color.RED);
add(myOval);
}
}
Condition that I will work on in part 2:
Do you make appropriate use of constants? Several of the programs you’ll write – especially
the graphics programs – will require values that will not be immediately evident from context.
When appropriate, introduce constants into your program to make the program more
customizable and easier to read.
Here is the code that contains the constants. So for example, the boss wants to make the logo bigger, replacing the value of the constants is easier:
import acm.graphics.*;
import acm.program.*;
import java.awt.*;
public class Target extends GraphicsProgram {
final static double firstOvalxUpLeft = 64;
final static double firstOvalyUpLeft = 64;
final static double firstOvalHeight = 72;
final static double firstOvalWidth = 72;
final static double secondOvalxUpLeft = 76.6;
final static double secondOvalyUpLeft = 76.6;
final static double secondOvalHeight = 46.8;
final static double secondOvalWidth = 46.8;
final static double thirdOvalxUpLeft = 89.2;
final static double thirdOvalyUpLeft = 89.2;
final static double thirdOvalHeight = 21.6;
final static double thirdOvalWidth = 21.6;
public void run() {
drawLargeRedOval();
drawWhiteOval();
drawSmallRedOval();
}
// precondition: a canvas of 200pixels across and 200pixels top to bottom,
// the center is 100x100 pixels.
// postcondition is a red filled circle with 1 inch radius with 72pixels has
// a center of 36
// 100 - 36 = 64,64 is where the left and bottom of the rectangle in which
// the oval is located should be placed
public void drawLargeRedOval() {
GOval myOval = new GOval(firstOvalxUpLeft, firstOvalyUpLeft,
firstOvalHeight, firstOvalWidth);
myOval.setFilled(true);
myOval.setColor(Color.RED);
myOval.setFillColor(Color.RED);
add(myOval);
}
// precondition: a 200x200pxl canvas with a 72pxl red circle centered at
// 100x100
// postcondition: another white circle added on top of the red circle. .65
// of 72 = 46.8 - half of 46.8 = 23.4
// 100 - 23.4 = 76.6, is where the left and bottom of the GOval rectangle is
// set.
public void drawWhiteOval() {
GOval myOval = new GOval(secondOvalxUpLeft, secondOvalyUpLeft,
secondOvalHeight, secondOvalWidth);
myOval.setFilled(true);
myOval.setColor(Color.WHITE);
myOval.setFillColor(Color.WHITE);
add(myOval);
}
// precondition: a 200x200pxl canvas with a 46.8 white circle on top of a
// red 72pxl circle with a center of 100x100
// post condition: another red circle added on top of the white circle. .3
// of 72 = 21.6 - half of 21.6 = 10.8
// 100 - 10.8 = 89.2, is where the left and bottom of the small re oval is
// set.
public void drawSmallRedOval() {
GOval myOval = new GOval(thirdOvalxUpLeft, thirdOvalyUpLeft,
thirdOvalHeight, thirdOvalWidth);
myOval.setFilled(true);
myOval.setColor(Color.RED);
myOval.setFillColor(Color.RED);
add(myOval);
}
}