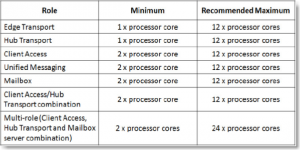
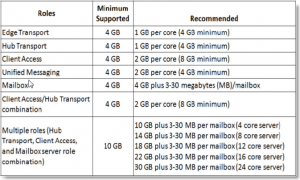
If you have recently enabled MFA multi factor authentication or 2FA on your Office 365 tenant, your Microsoft Outlook for Office 365 MSO 16.0.11929 (desktop version) users may be prompted over and over for their password, even though you are sure you have the correct password and even the apppassword / app password hash. I’m sure you’ve tried to re-configure Outlook, look at Azure settings, reinstall Outlook, check your autodiscover records, make sure you have the correct Office Suite version and perhaps have even attempted to change the windows 10 registry with the following settings:
[HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Outlook\AutoDiscover] "ExcludeExplicitO365Endpoint"=dword:00000001 [HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Outlook\AutoDiscover] "ExcludeLastKnownGoodUrl"=dword:00000001 [HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Outlook\AutoDiscover] "ExcludeHttpsRootDomain"=dword:00000001 [HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Outlook\AutoDiscover] "ExcludeSrvRecord"=dword:00000001
However doing these things did not resolve the issue, and the only fix that worked for us, was to follow the instructions on how to enable modern authentication for Exchange Online here: https://docs.microsoft.com/en-us/exchange/clients-and-mobile-in-exchange-online/enable-or-disable-modern-authentication-in-exchange-online
So I thought it would be helpful to have a step-by-step how to enable modern authentication in Exchange Online for Office 365 based on the instructions provided in the link above.
With MFA enabled, connecting to Exchange Online with powershell is not as simple as it used to be, but still not all that bad. I’ve found the easiest way to connect to Exchange Online with Powershell is to do the following.
Note: A forewarning here, with certain browsers, when clicking on the Exchange Hybrid “Configure” button, and then installing the Hybrid configuration, the Office 365 login screen may may flash on the screen as a white box, and then disappears before you can authenticate and use your 2FA txt code. I’ve seen this when using Microsoft Edge, Chrome, and even the new version of Microsoft Edge based on Chromium. The only browser I’ve gotten this to consistently work with is the Internet Explorer browser built into Windows 10. The Internet Explorer browser is installed on Windows 10 by default, it’s hidden in the start menu under Accessories:
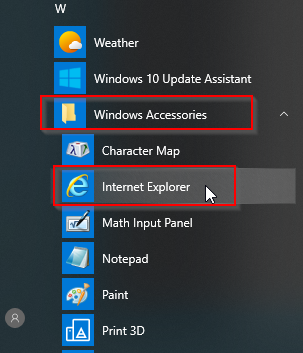
If you do attempt to run the Exchange Powershell Module using chrome you may encounter the error:
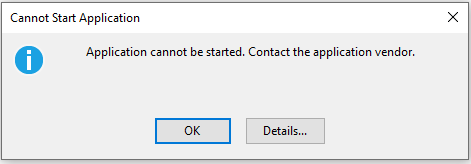
“Application cannot be started. Contact the application vendor.”
When clicking the Details… button, you may find information similar to the following:
PLATFORM VERSION INFO Windows : 10.0.18363.0 (Win32NT) Common Language Runtime : 4.0.30319.42000 System.Deployment.dll : 4.8.3752.0 built by: NET48REL1 clr.dll : 4.8.4121.0 built by: NET48REL1LAST_C dfdll.dll : 4.8.3752.0 built by: NET48REL1 dfshim.dll : 10.0.18362.1 (WinBuild.160101.0800) SOURCES Deployment url : file:///C:/Users/Jason/Downloads/Microsoft.Online.CSE.PSModule.Client%20(3).application IDENTITIES Deployment Identity : Microsoft.Online.CSE.PSModule.Client.application, Version=16.0.3527.0, Culture=neutral, PublicKeyToken=45baf49ae30bdb15, processorArchitecture=msil APPLICATION SUMMARY * Installable application. * Trust url parameter is set. ERROR SUMMARY Below is a summary of the errors, details of these errors are listed later in the log. * Activation of C:\Users\Jason\Downloads\Microsoft.Online.CSE.PSModule.Client (3).application resulted in exception. Following failure messages were detected: + Deployment and application do not have matching security zones. COMPONENT STORE TRANSACTION FAILURE SUMMARY No transaction error was detected. WARNINGS There were no warnings during this operation. OPERATION PROGRESS STATUS * [4/3/2020 3:32:57 PM] : Activation of C:\Users\Jason\Downloads\Microsoft.Online.CSE.PSModule.Client (3).application has started. * [4/3/2020 3:32:57 PM] : Processing of deployment manifest has successfully completed. * [4/3/2020 3:32:57 PM] : Installation of the application has started. ERROR DETAILS Following errors were detected during this operation. * [4/3/2020 3:32:57 PM] System.Deployment.Application.InvalidDeploymentException (Zone) - Deployment and application do not have matching security zones. - Source: System.Deployment - Stack trace: at System.Deployment.Application.DownloadManager.DownloadApplicationManifest(AssemblyManifest deploymentManifest, String targetDir, Uri deploymentUri, IDownloadNotification notification, DownloadOptions options, Uri& appSourceUri, String& appManifestPath) at System.Deployment.Application.ApplicationActivator.DownloadApplication(SubscriptionState subState, ActivationDescription actDesc, Int64 transactionId, TempDirectory& downloadTemp) at System.Deployment.Application.ApplicationActivator.InstallApplication(SubscriptionState& subState, ActivationDescription actDesc) at System.Deployment.Application.ApplicationActivator.PerformDeploymentActivation(Uri activationUri, Boolean isShortcut, String textualSubId, String deploymentProviderUrlFromExtension, BrowserSettings browserSettings, String& errorPageUrl, Uri& deploymentUri) at System.Deployment.Application.ApplicationActivator.PerformDeploymentActivationWithRetry(Uri activationUri, Boolean isShortcut, String textualSubId, String deploymentProviderUrlFromExtension, BrowserSettings browserSettings, String& errorPageUrl) --- End of stack trace from previous location where exception was thrown --- at System.Runtime.ExceptionServices.ExceptionDispatchInfo.Throw() at System.Deployment.Application.ApplicationActivator.PerformDeploymentActivationWithRetry(Uri activationUri, Boolean isShortcut, String textualSubId, String deploymentProviderUrlFromExtension, BrowserSettings browserSettings, String& errorPageUrl) at System.Deployment.Application.ApplicationActivator.ActivateDeploymentWorker(Object state) COMPONENT STORE TRANSACTION DETAILS No transaction information is available.
At this point, it may be necessary to uninstall the existing module and then re-install and run using Internet Explorer. You may even receive the following error:
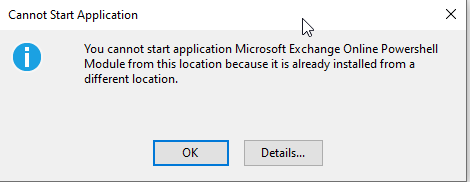
"You cannot start application Microsoft Exchange Online Powershell Module from this location because it is already installed from a different location."
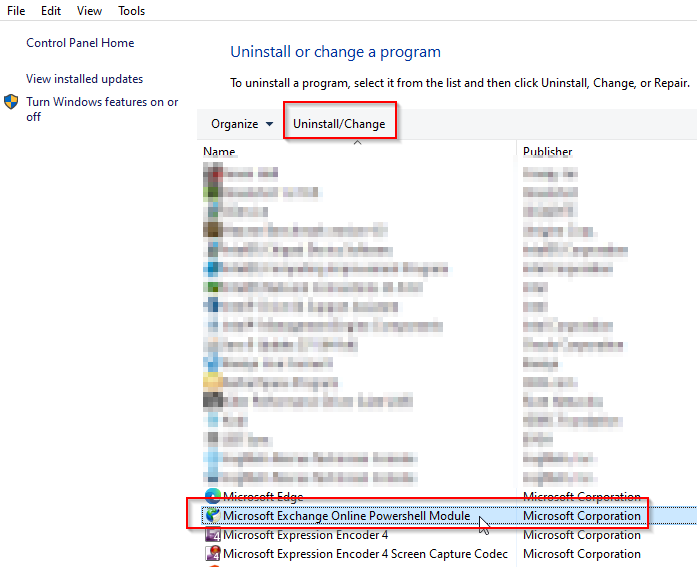
To uninstall the module, click the Start Button > type “appwiz.cpl” and press Enter.
Inside of the Programs and Features screen find the application and click Uninstall.
After uninstall, log into your tenant (with an administrator account) at https://www.office.com using Internet Explorer 11, and click the Admin link:
Next, Expand the Menu on the left menu by clicking Show All… and then click on Exchange:
Next we want to click on the Hybrid link to get to our Powershell Configure button:
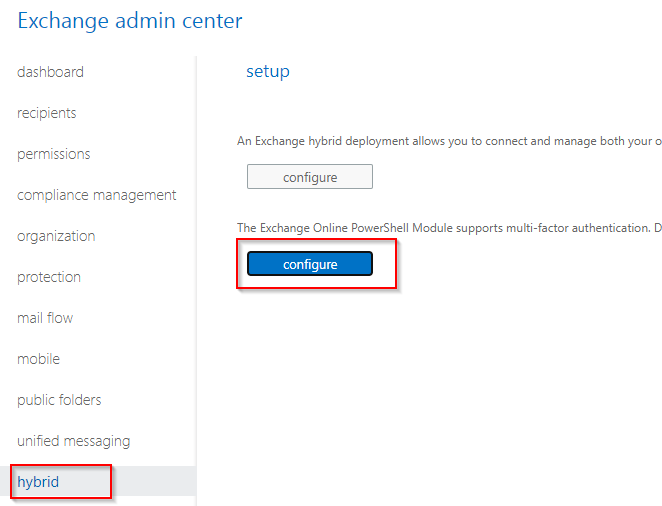
Go ahead and install the component if it asks, and when it completes, you’ll be greeted with a Windows Powershell screen with the following message:
Experience the fast and reliable Exchange PowerShell V2 Cmdlets via new PowerShellGallery module. Go to https://aka.ms/exops-docs This PowerShell module allows you to connect to Exchange Online service. To connect, use: Connect-EXOPSSession -UserPrincipalName <your UPN> This PowerShell module allows you to connect Exchange Online Protection and Security & Compliance Center services also. To connect, use: Connect-IPPSSession -UserPrincipalName <your UPN> To get additional information, use: Get-Help Connect-EXOPSSession, or Get-Help Connect-IPPSSession
We now want to initiate our session using the instructions provided. At the prompt, type in the command:
Connect-EXOPSSession -UserPrincipalName [email protected]
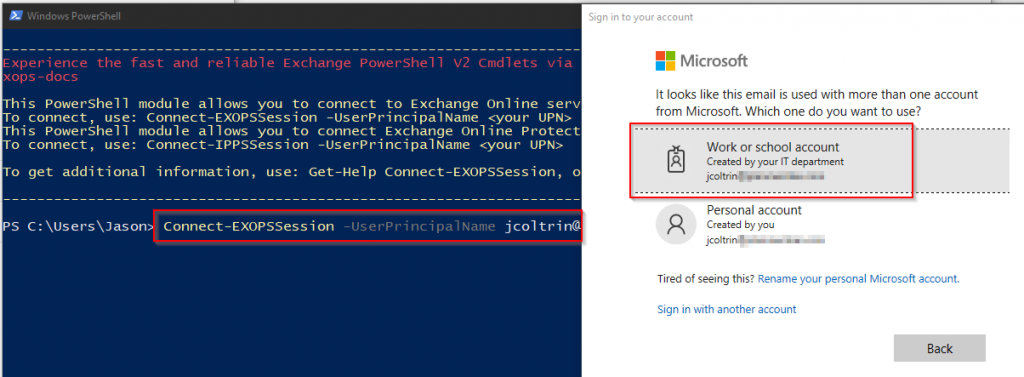
You’ll now be prompted to sign into your tenant (Work or School). You’ll see some status bars go by and then be prompted with a warning about unapproved verbs (for example banish?)
So now we want to (only look before making changes) get our organization structure, and more precisely, find the status of our OAuth2ClientProfileEnabled setting by issuing the command:
Get-OrganizationConfig | Format-Table Name,OAuth* -Auto
Your output should look similar to the following (with the exception being that your result will probably be set to False:)
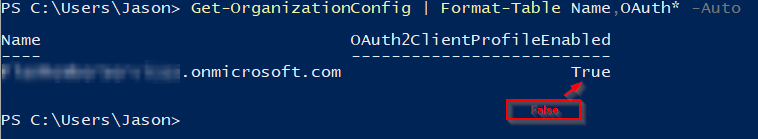
Finally we can set this to True by using the following command:
Set-OrganizationConfig -OAuth2ClientProfileEnabled $true
To verify the command was successful, run the previous command again:
Get-OrganizationConfig | Format-Table Name,OAuth* -Auto
That’s about it! Give the setting about an hour to propagate and then try testing Outlook on the desktop again. You may get a few clients where their profile needs to be recreated. You can do this by going into the control panel > (1) choose Small Icons > (2) Mail Microsoft Outlook 2016.
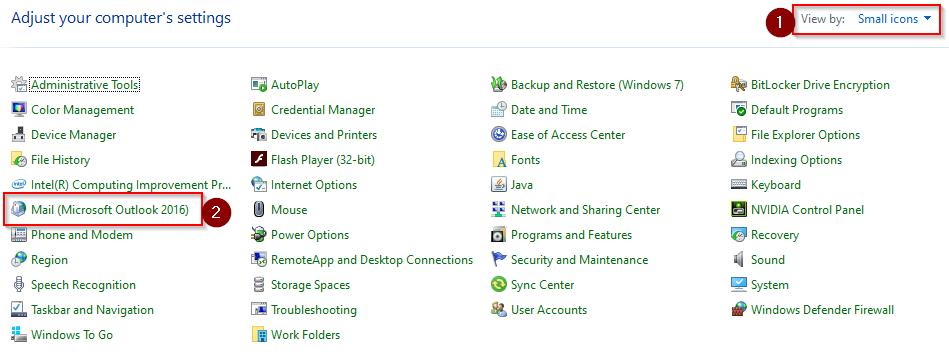
Then click Show Profiles
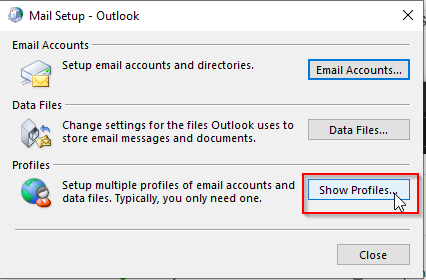
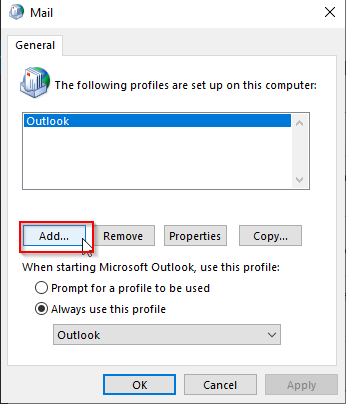
Click Add…
Now when setting up the new mail account, you should be prompted with the modern authentication and you’ll be prompted for your txt code or Microsoft Authentication Application.