How do I get all of the DNS records for a domain using the dig command in only “Answer Section” (+answer) format? The command should return A, MX, NS, TXT, SOA and CNAME records.
Normally using the “any” flag, we would get all of this information at once, however, when attempting to run a dig command with the ‘any’ switch, we do not get the DNS records we want:
dig jasoncoltrin.com anyThe above command returns an answer section with only: “RFC8428” “”
According to chatgpt, this means that the ‘any’ query type is not guaranteed to return all the records for a given name, and some DNS servers may choose to return an empty answer instead. This is done to improve the performance and security of the DNS system.
Still, I want to have a single command to get the most information at once, and the following command does so, however, writing the command is impractical:
dig +noall +answer +multi jasoncoltrin.com A jasoncoltrin.com MX jasoncoltrin.com NS jasoncoltrin.com TXT jasoncoltrin.com SOA jasoncoltrin.com CNAME
I also tried the following with no luck:
dig +noall +answer jasoncoltrin.com A,MX,NS,TXTThis only returned the A records.
So instead, we can use a bash script to create a $domain variable, and have the script use the ‘read’ command to prompt us for the domain name:
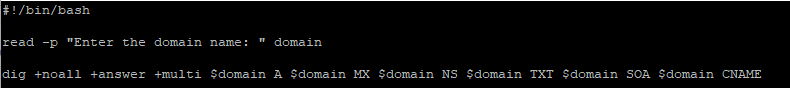
#!/bin/bash
read -p "Enter the domain name: " domain
dig +noall +answer +multi $domain A $domain MX $domain NS $domain TXT $domain SOA $domain CNAME
To write the script, do the following:
vi digdomain.sh
(insert) > copy/paste script > (Escape) > :wq
Then make the script executable with the command:
chmod +x digdomain.sh
Run the command using the ./ prefix:
./digdomain.shWhen we run the script, we’re prompted for the domain name, then the result is most of the information we want in an easy-to-read format:
jason@ubuntu0:~$ ./digdomain.sh
Enter the domain name: jasoncoltrin.com
jasoncoltrin.com. 118 IN A 172.67.196.181
jasoncoltrin.com. 118 IN A 104.21.44.69
jasoncoltrin.com. 1854 IN MX 10 mailstore1.secureserver.net.
jasoncoltrin.com. 1854 IN MX 0 smtp.secureserver.net.
jasoncoltrin.com. 5652 IN NS daisy.ns.cloudflare.com.
jasoncoltrin.com. 5652 IN NS lee.ns.cloudflare.com.
jasoncoltrin.com. 300 IN TXT "Currently located in a black hole\" \"Likely to be eaten by a grue"
jasoncoltrin.com. 300 IN TXT "google-site-verification=key"
jasoncoltrin.com. 300 IN TXT "google-site-verification=key"
jasoncoltrin.com. 2052 IN SOA daisy.ns.cloudflare.com. dns.cloudflare.com. (
2305113011 ; serial
10000 ; refresh (2 hours 46 minutes 40 seconds)
2400 ; retry (40 minutes)
604800 ; expire (1 week)
3600 ; minimum (1 hour)
)
This made me happy because I had forgotten about my easter egg TXT record. 🙂